DSC composite resource for auto administrator logon
For my lab setup, I sometimes need to enable auto administrator logon during OS and application deployment. I use DSC for most part of this automation and what is better than a DSC resource for this?
Auto administrator logon is enabled by making changes to the HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\WinLogon registry key. To enable auto administrator logon, we need to add the following values:
- AutoAdminLogon (REG_SZ) with a value of 1
- DefaultUserName (REG_SZ) with the user name as the value
- DefaultPassword (REG_SZ) with the user password as the value
- DefaultDomainName (REG_SZ) with the domain name of the user as the value
To disable auto administrator logon, we can simply set the AutoAdminLogon to 0 or delete all the above values. Now, coming back to DSC, there is a DSC registry resource. So, there is no need to re-invent the wheel. Instead, we can simply create a composite resource to do this. The following configuration script combines all the registry entries that need to be configured for the auto administrator logon.
Configuration AutoAdminLogon {
Param (
[Parameter(Mandatory)]
[PSCredential] $AutoAdminCredential,
[Parameter()]
[ValidateSet("Present","Absent")]
[String]$Ensure = "Present"
)
$Key = 'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon'
#Get the default domain name from the credential object
if ($AutoAdminCredential.GetNetworkCredential().Domain) {
$DefaultDomainName = $AutoAdminCredential.GetNetworkCredential().Domain
} else {
$DefaultDomainName = ""
}
Registry DefaultDomainName
{
Ensure = $Ensure
Key = $Key
ValueName = 'DefaultDomainName'
ValueData = $DefaultDomainName
}
Registry DefaultUserName
{
Ensure = $Ensure
Key = $Key
ValueName = 'DefaultUserName'
ValueData = $AutoAdminCredential.GetNetworkCredential().UserName
}
Registry DefaultPassword
{
Ensure = $Ensure
Key = $Key
ValueName = 'DefaultPassword'
ValueData = $AutoAdminCredential.GetNetworkCredential().Password
}
Registry AutoAdminLogon
{
Ensure = $Ensure
Key = $Key
ValueName = 'AutoAdminLogon'
ValueData = 1
}
}
In the above configuration, I have used PSCredential type to collect the username and password instead of plain-text strings. Also, the Ensure value indicates whether we want to set the auto administrator logon or remove it. These are the only two parameters we need. The DefaultDomainName will be derived from the PSCredential object. The default ValueType for registry values is REG_SZ and there is no need to provide that property within the resource instance configuration.
To be able to use this configuration as a composite resource, we need to save it as
New-ModuleManifest -Path .\AutoAdminLogon.psd1 -RootModule .\AutoAdminLogon.Schema.psm1
Once we have the manifest file created, we need to store this in the modules location. Here is how I stored it.
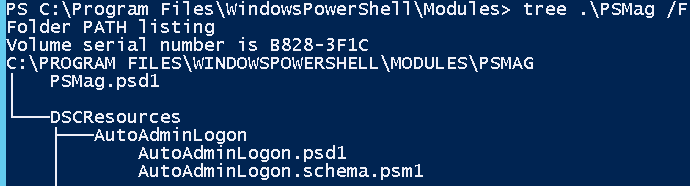
We need to create a DSCResources folder and store the PSM1 and PSD1 files under that. This can, now, be used to configure AutoAdminLogon using DSC. Here is a sample configuration script:
$ConfigData = @{
AllNodes = @(
@{ NodeName = "*"; PsDscAllowPlainTextPassword = $true },
@{ NodeName = 'WMF5-1' }
)
}
Configuration Demo {
Param (
[pscredential]
$AutoAdminCredential
)
Import-DscResource -Name AutoAdminLogon
AutoAdminLogon Demo2 {
AutoAdminCredential = $AutoAdminCredential
Ensure = "Present"
}
}
Demo -ConfigurationData $ConfigData -AutoAdminCredential (Get-Credential)
This configuration script ensures that auto administrator logon gets set on the target system. I have used plain-text credentials in this example. However, this should work seamlessly with encrypted credentials as well.
Share on: